Azure Key Vault Generate Csr
This is a proof of concept showing how to generate PKCS7 signatures using certificates in Azure Key Vault. TheSignedCms class in .NET does not have the extensibility today to enable this. As such, I've used Bouncy Castle'smethods to create that and ensure interop with the SignedCms one.
- Part 2 of 3: Generating the Certificate Signing Request (CSR) The Certificate Signing Request (CSR) will be generating from within Microsoft Azure KeyVault as follows: 1.
- Apr 17, 2017 Using Azure Key Vault with PowerShell – Part 1 Azure Key Vault is used to safeguard and manage cryptographic keys, certificates and secrets used by cloud applications and services (you can still consume these on-premise though).
- Dec 05, 2013 Key Vault Safeguard and maintain control of keys. Obtaining a Certificate for use with Windows Azure Web Sites (WAWS) Posted on December 5, 2013. Create a CSR using DigiCert’s Certificate Utility DigiCert’s Certificate Utility is a 3 rd party tool that was designed to make the process of generating a CSR easier by providing a.
- Below is the PowerShell commands to generate the.pfx file from the Azure Key Vaults. Step 1 Log in to Azure using the below command and provide required credentials.
Azure Key Vault customers can order DigiCert SSL Certificates directly from their Key Vault account through the CertCentral REST API. Certificates are automatically renewed, making sure that lapses in SSL/TLS security don't happen. Note: It's possible to define Key Vault Access Policies both within the azurermkeyvault resource via the accesspolicy block and by using the azurermkeyvaultaccesspolicy resource.However it's not possible to use both methods to manage Access Policies within a KeyVault, since there'll be conflicts. 2) Creating a Private Key and Certificate Signing Request (CSR) 3) Importing the Public Signed Certificate to Microsoft Azure KeyVault. Part 1 of 3: Login and Create a Resource Group. Launch Microsoft Azure PowerShell. Log in to your Microsoft Azure account by typing: Login-AzureRmAccount.
Setup
To run these tests, you'll need to import a code signing certificate into anAzure Key Vault. You can do this by importing the PFX for certs you already have,or, the harder way, by generating a CSR in the HSM and using that for an EV CodeSigning certificate. You will also need to create a new RSA key using Add-AzureKeyVaultKey orthe UI mentioned below. Use the key name as the azureKeyVaultKeyName in theconfig and the certificate name as the azureKeyVaultCertificateName.
Create a service principal / application and grant it access to the Key Vault with the followingpermissions:
| Category | Permission |
|---|---|
| Key | Get, Sign |
| Certificate | Get |
You'll need to drop a json file called azure-creds.json in the tests private directorywith the following values:
You'll also need to drop a json file called config.json in the tests private directorywith the following values. Should be a thumbprint of a cert with a private key in the user store:
Azure Key Vault Explorer
There's a handy GUI for accessing Key Vault and includes support for importing certificates:https://github.com/elize1979/AzureKeyVaultExplorer
The app defaults to logging into an @microsoft.com account, so if you want to connect to adifferent directory, you need to change the settings first. Change the Authority to https://login.windows.net/commonand edit the DomainHints value to have your AAD domain(s) in it.
The following scenarios outline several of the primary usages of Key Vault’s certificate management service including the additional steps required for creating your first certificate in your key vault.
The following are outlined:
- Creating your first Key Vault certificate
- Creating a certificate with a Certificate Authority that is partnered with Key Vault
- Creating a certificate with a Certificate Authority that is not partnered with Key Vault
- Import a certificate
Certificates are complex objects
Certificates are composed of three interrelated resources linked together as a Key Vault certificate; certificate metadata, a key, and a secret.
Creating your first Key Vault certificate
Before a certificate can be created in a Key Vault (KV), prerequisite steps 1 and 2 must be successfully accomplished and a key vault must exist for this user / organization. Microsoft office standard 2016 product key generator.
Step 1 - Certificate Authority (CA) Providers
- On-boarding as the IT Admin, PKI Admin or anyone managing accounts with CAs, for a given company (ex. Contoso) is a prerequisite to using Key Vault certificates.
The following CAs are the current partnered providers with Key Vault:- DigiCert - Key Vault offers OV TLS/SSL certificates with DigiCert.
- GlobalSign - Key Vault offers OV TLS/SSL certificates with GlobalSign.
Step 2 - An account admin for a CA provider creates credentials to be used by Key Vault to enroll, renew, and use TLS/SSL certificates via Key Vault.
Step 3 - A Contoso admin, along with a Contoso employee (Key Vault user) who owns certificates, depending on the CA, can get a certificate from the admin or directly from the account with the CA.
- Begin an add credential operation to a key vault by setting a certificate issuer resource. A certificate issuer is an entity represented in Azure Key Vault (KV) as a CertificateIssuer resource. It is used to provide information about the source of a KV certificate; issuer name, provider, credentials, and other administrative details.
Ex. MyDigiCertIssuer
- Provider
- Credentials – CA account credentials. Each CA has its own specific data.
For more information on creating accounts with CA Providers, see the related post on the Key Vault blog.
Step 3.1 - Set up certificate contacts for notifications. This is the contact for the Key Vault user. Key Vault does not enforce this step.
Note - This process, through step 3.1, is a onetime operation.
Creating a certificate with a CA partnered with Key Vault
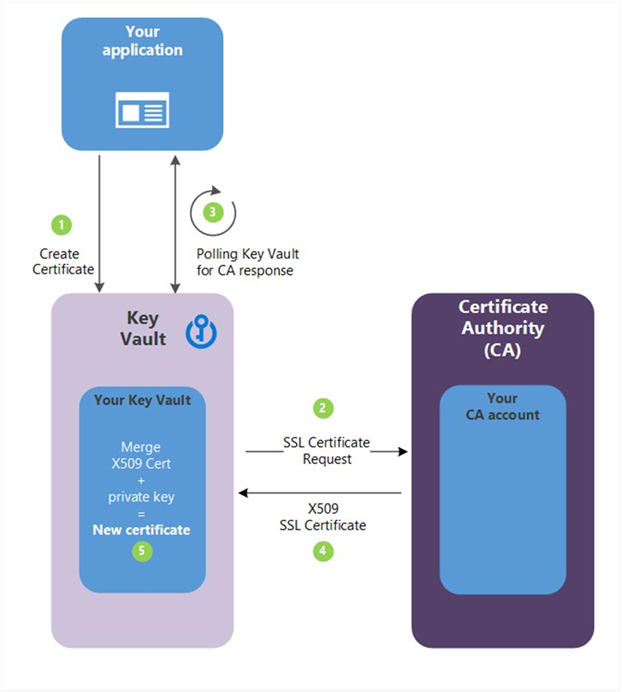
Step 4 - The following descriptions correspond to the green numbered steps in the preceding diagram.
(1) - In the diagram above, your application is creating a certificate which internally begins by creating a key in your key vault.
(2) - Key Vault sends an TLS/SSL Certificate Request to the CA.
(3) - Your application polls, in a loop and wait process, for your Key Vault for certificate completion. The certificate creation is complete when Key Vault receives the CA’s response with x509 certificate.
(4) - The CA responds to Key Vault's TLS/SSL Certificate Request with an X509 TLS/SSL Certificate.
(5) - Your new certificate creation completes with the merger of the X509 Certificate for the CA.
Key Vault user – creates a certificate by specifying a policy
Repeat as needed
Policy constraints
- X509 properties
- Key properties
- Provider reference - > ex. MyDigiCertIssure
- Renewal information - > ex. 90 days before expiry
A certificate creation process is usually an asynchronous process and involves polling your key vault for the state of the create certificate operation.
Get certificate operation- Status: completed, failed with error information or, canceled
- Because of the delay to create, a cancel operation can be initiated. The cancel may or may not be effective.
Import a certificate
Alternatively – a cert can be imported into Key Vault – PFX or PEM.
Import certificate – requires a PEM or PFX to be on disk and have a private key.
You must specify: vault name and certificate name (policy is optional)
PEM / PFX files contains attributes that KV can parse and use to populate the certificate policy. If a certificate policy is already specified, KV will try to match data from PFX / PEM file.
Once the import is final, subsequent operations will use the new policy (new versions).
If there are no further operations, the first thing the Key Vault does is send an expiration notice.
Also, the user can edit the policy, which is functional at the time of import but, contains defaults where no information was specified at import. Ex. no issuer info
Formats of Import we support
We support the following type of Import for PEM file format. A single PEM encoded certificate along with a PKCS#8 encoded, unencrypted key which has the following
-----BEGIN CERTIFICATE----------END CERTIFICATE-----
-----BEGIN PRIVATE KEY----------END PRIVATE KEY-----
On certificate merge we support 2 PEM based formats. You can either merge a single PKCS#8 encoded certificate or a base64 encoded P7B file.-----BEGIN CERTIFICATE----------END CERTIFICATE-----
We currently don't support EC keys in PEM format.
Creating a certificate with a CA not partnered with Key Vault
This method allows working with other CAs than Key Vault's partnered providers, meaning your organization can work with a CA of its choice.
The following step descriptions correspond to the green lettered steps in the preceding diagram.
(1) - In the diagram above, your application is creating a certificate, which internally begins by creating a key in your key vault.
Azure Key Vault Documentation
(2) - Key Vault returns to your application a Certificate Signing Request (CSR).
(3) - Your application passes the CSR to your chosen CA.
Azure Key Vault Generate Certificate
(4) - Your chosen CA responds with an X509 Certificate.
(5) - Your application completes the new certificate creation with a merger of the X509 Certificate from your CA.